Recently, I started setting up my own SIEM and XDR lab using Microsoft Sentinel and Microsoft Defender. In this guide, I’ll walk you through how I connected a Linux VM running in an on-premises environment (outside of Azure) to Sentinel to collect and analyze syslogs within the SIEM.
1. Installing the Azure Arc Agent
To onboard the Linux VM to Azure Arc , install the Azure Connected Machine Agent:
curl -sSL https://gbl.his.arc.azure.com/azcmagent-linux | bash
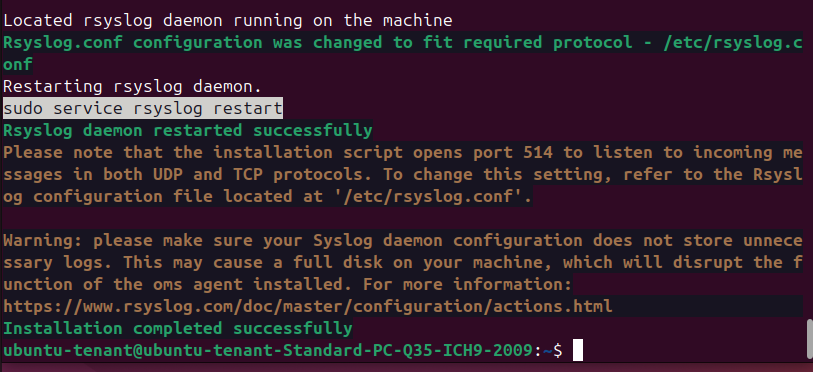
2. Installing the AMA Syslog Forwarder
To forward syslog data to Sentinel, install the Azure Monitor Agent (AMA) Syslog Forwarder :
sudo wget -O Forwarder_AMA_installer.py https://raw.githubusercontent.com/Azure/Azure-Sentinel/master/DataConnectors/Syslog/Forwarder_AMA_installer.py
sudo python3 Forwarder_AMA_installer.py
3. Retrieving Required Azure Details
Before connecting our VM to Azure Arc, we need to collect key details. We can retrieve them using Azure Cloud Shell:
- Find your Subscription ID:
az account show --query id -o tsv - List available Resource Groups:
az group list --query "[].{Name:name}" -o table - List available Azure Locations:
az account list-locations --query "[].{Name:name}" -o table
4. Assigning Required Permissions
Ensure your account has the necessary roles as specified in the Azure Arc prerequisites .
Assign “Azure Connected Machine Onboarding” Role
az role assignment create --assignee <your-email-or-service-principal-id> --role "Azure Connected Machine Onboarding" --scope /subscriptions/<subscription-id>/resourceGroups/SENTINEL-2025
Assign “Contributor” Role
az role assignment create --assignee <your-email-or-service-principal-id> --role "Contributor" --scope /subscriptions/<subscription-id>/resourceGroups/SENTINEL-2025
5. Registering Required Azure Resource Providers
To enable proper integration, register the required Azure Resource Providers:
az provider register --namespace Microsoft.HybridCompute
az provider register --namespace Microsoft.GuestConfiguration
az provider register --namespace Microsoft.HybridConnectivity
Verify the registration status:
az provider show --namespace Microsoft.HybridCompute --query "registrationState"
az provider show --namespace Microsoft.GuestConfiguration --query "registrationState"
az provider show --namespace Microsoft.HybridConnectivity --query "registrationState"
6. Connecting the Machine to Azure Arc
Now, we connect the Linux VM to Azure Arc:
azcmagent connect --location eastus --resource-group SENTINEL-2025 --subscription-id <fake-subscription-id>
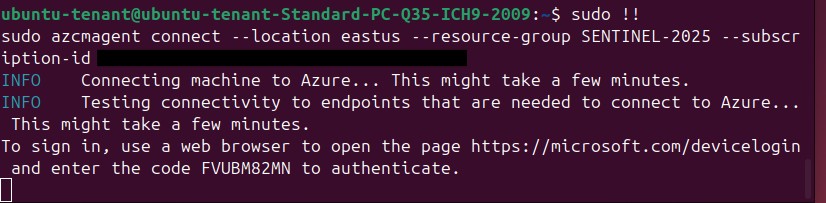
Follow the authentication process via Microsoft Device Login .
7. Configuring Data Collection for Syslogs
With the VM connected, we can now create a Data Collection Rule (DCR) to collect syslog events. For example, to retrieve LOG_AUDIT and LOG_AUTHPRIV from syslog:
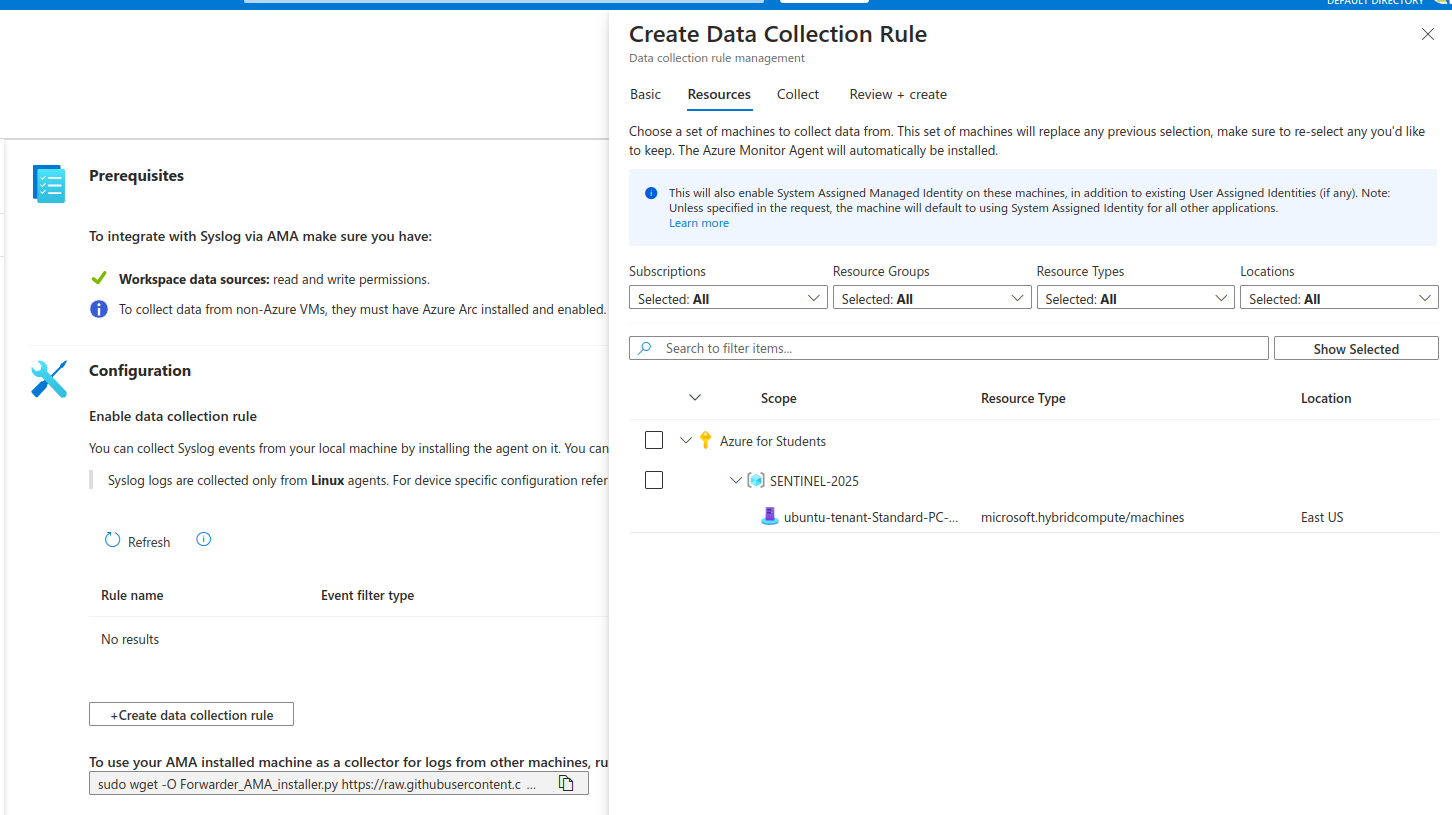
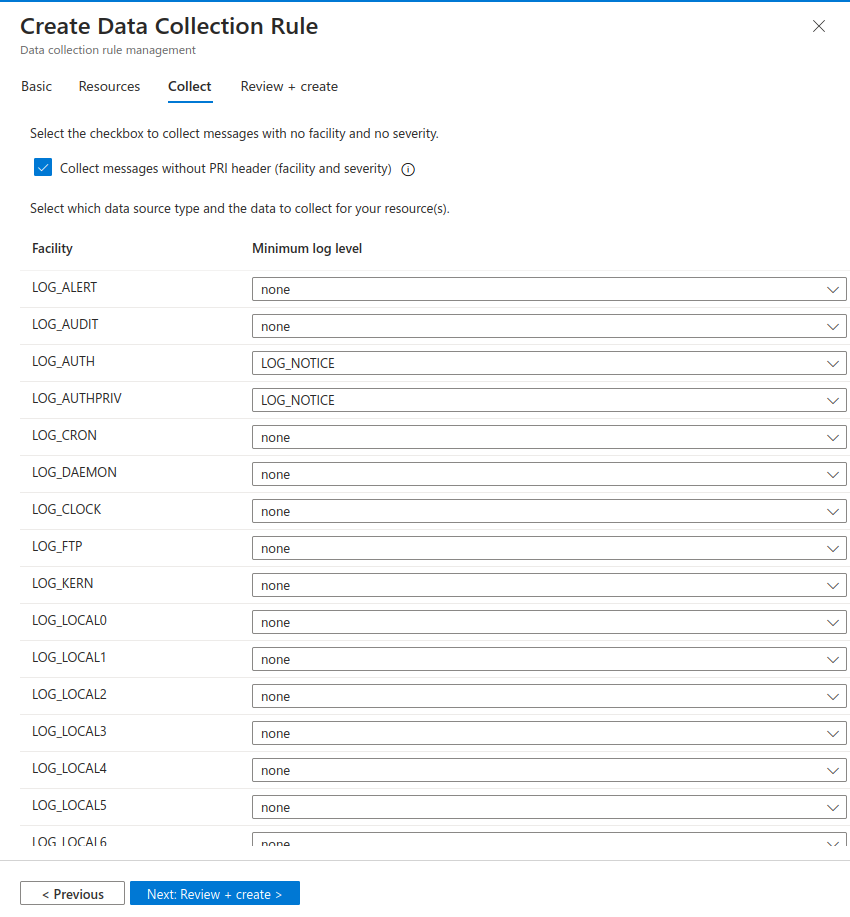
Different DCRs can be configured based on the VM’s role and data ingestion requirements. For more details, refer to Syslog Data Collection .
8. Creating Analytic Rules in Sentinel
With syslog data flowing into Sentinel, we can now set up analytic rules to trigger alerts and incidents. Here’s an example of an incident created for “Failed logon attempts in authpriv”:
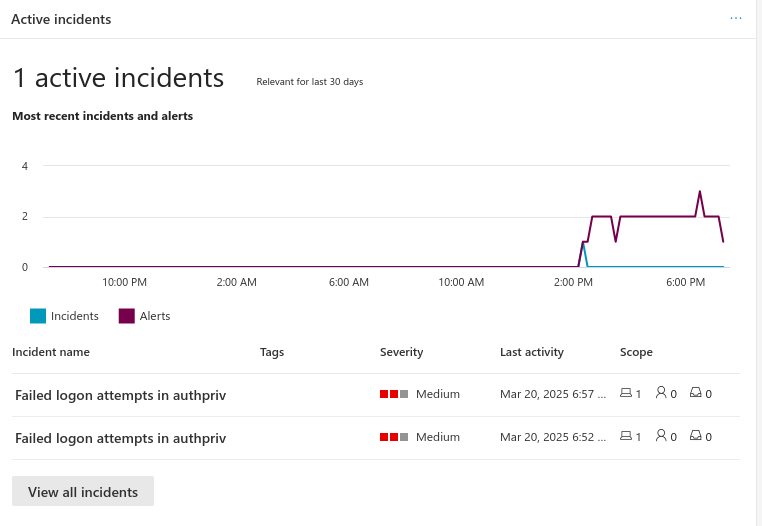
Conclusion
By following these steps, we successfully connected an on-premises Linux VM to Microsoft Sentinel using Azure Arc and the Azure Monitor Agent (AMA) Syslog Forwarder. This setup enables real-time syslog collection, threat detection, and incident response within the SIEM.
As I continue building my SIEM and XDR lab, I’ll be exploring more advanced log analysis, automation, and threat-hunting techniques. Stay tuned for future posts where I’ll dive deeper into custom detection rules, playbooks, and integration with Microsoft Defender to enhance security monitoring and response capabilities.